The term ‘Trojan Horse’ goes back to the story of Troy war! In that war, Greeks had created a wooden horse and had stuffed soldiers inside it; and the horse was gifted to the city of Troy. Upon getting inside the gate, the wooden horse was burst out and the soldiers started attacking the City of Troy. Now, we hear the same term in association with the computing sector, where Trojan horse is considered a major computer threat, just like viruses, malware, spyware etc that have an adversary effect on your computer, your data and your activities. In this article, we can go deep into the different aspects of Trojan horse computer malware and how it can be removed from the PC manually.

What is Trojan Horse
As we said, it’s a major threat that we deal with in the world of computing. Even so, unlike what the majority thinks, it is not a virus. Viruses are characterized by its capacity to spread themselves into different parts of the device once it has been inserted into one device. However, Trojan horse does not spread. On the other hand, if a Trojan has been made its way into one device, it starts deleting important files you have in your device and opening backdoors, using which the evil hands can have access to your device and data. Trojan Horse is considered one of the most used ways of computer hacking and the way it functions is quite interesting, per se.
Read: Benefits of Antivirus Programs
How Trojan Horse Work
As the story in War of Troy, Trojan horse malware is disguised as a useful tool and is spread. At the first look, it might be a quite useful tool for your computer — and, of course, the masses will download the tool and install it. However, if the installation is over, the real face of Trojan horse can be seen. Because this nature of presentations, people do not always know if the PC is affected by Trojan horse attacks.
What Harm Trojan Horse Can Do?
As we mentioned earlier, it is meant to delete important files and to open backdoors to the hackers. If one backdoor has been created, that can be used by the hackers and other evil hands to get access to the computer. The main sets of issues that may be caused by Trojan horse are:
-
File Stealing
In some cases, Trojan horses create a FTP File Server in the affected computer, to which the hacker has access. Using this server, the hacker can do file transfer between the affected device. That is, the confidential files are downloaded by the hacker whereas he can insert some extra-malicious stuff into the PC.
-
Remote Access of Your PC
This might sound surprising, but the Trojan horse threats are cleverly used to get remote access of one device, and in most cases, the user of affected PC does not know the issue that is happening. The only symptom you can see is that the network resource usage and system resource usage are way too high. Using the remote access option, the user is able to do pretty much anything with your PC.
-
Key Logging and Password Stealing
Just as the case of some computer viruses, Trojans can be used as key loggers as well. It means that if your PC has an effectual Trojan in it, the tool might be tracking your keystrokes and communicating the data with the hacker. It isn’t limited to keystrokes, because the options include screenshot snapping. In the same way, password stealing would be done by Trojan horse tools, and the data is communicated with the hacker via emails.
These are just the major issues, but others include DDoS. So, it’s important to know whether your PC has one Trojan horse virus in it.
How to Know if a PC is Infected by Trojan Horse?

The best way to know if there’s a Trojan horse in your computer is to use an effective antivirus tool. Nowadays, most of antivirus tools have been packed with a Trojan scanning and removal options. It means that you will be able to get these Trojan-related files removed. Apart from this method, some characteristics of your PC may be the result of the Trojan attack.
- Continuous, Regular lagging of your PC
- System Resource usage would be quite high
- Network usage becomes high, even when you do nothing
If you see these issues regularly, you should seriously doubt that there’s a Trojan horse virus in your PC.
How to Remove Trojan Horse

There are two major methods available to remove Trojan horse from affected computers.
Method #1 — Use an Anti-virus Security Suite
If you want to escape from not just one Trojan but also the other threats you may find in future, it’s better to choose an effective antivirus software from the marketplace. Actually, there are many tools available such as Bitdefender, Kaspersky, Norton, Avast, McAfee and see other recommendations over here. Depending on the extra features you need, you can pick up one from reputed list of antivirus tools. Apart from that, there are some dedicated tools available for Trojan removal. You will be able to find many tools, both free and premium.
Method #2 — Manually Remove Trojan Horse (Not recommended)
In this, we have different steps to follow.
- First, you have to recognize the Trojan-affected area of your computer. This can be done using some kinds of scanning tools, such as Malwarebytes or the antivirus tool you have installed. Make sure you make the show hidden files on and Show system files as shown in the image of Folder option in Windows.
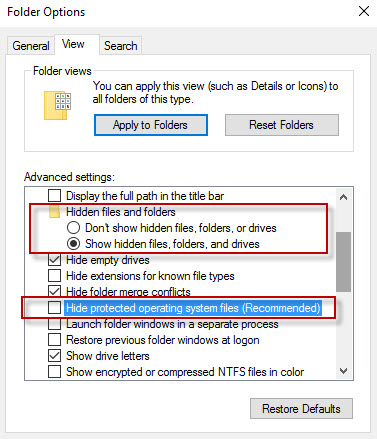
- In some cases of attacks, the PC would be showing DLL error, with the name of exe file. Thus, you will be able to find the Trojan.
- Before you begin the removal, you have to turn off system restore
- Restart your computer into Safe Mode. This can be done by pressing F8 when the system boots up and then selecting the ‘Safe Mode’
- When you are in the Safe Mode, you can go to the control panel and get rid of the software that is causing a Trojan attack. In addition, extensions of the software need to be removed — by deleting the corresponding folder from Windows drive.
If these steps have been followed well, your PC will be free from the Trojan attack. If that was successful, you should start seeing changes in terms of network usage and all, from the next time you boot up.
These are the two main methods to rely upon for removing Trojan horse from your computer. There are alternative methods such as process editing, but the completion of such methods requires good knowledge in Windows registry.
The Conclusion
So, we have given many details about Trojan horse computer threat and ways to remove it. There’s no doubt that a Trojan horse is a major threat to your privacy, data and functioning of your PC. So, once you have recognized it, you should use one of the best antivirus or the removal tools to get rid of Trojan horse.